Blog
You can become a superhero of automation and development by learning and practicing. This is our blog from our learnings and practice.
We are consultants and trainers in Cloud Foundry, devops automation and continous delivery. We have the best jobs in the world helping you have the best job in the world.

pgBadger is a helpful tool which will generate reports and diagrams about the type and pattern of sql queries over time that are submitted to PostgreSQL. The tool works by reading the PostgreSQL logs (not transaction logs) which are not typically enabled by default in the helm chart. Below are a few methods for leveraging

Unite! Summary: IBM’s Eirini Project allows Cloud Foundry’s runtime component to be replaced with Kubernetes. Combining these two technologies enables both operators and developers to be more productive. Technology executives and managers at large enterprises have a tough job in 2019 because the landscape of enterprise cloud IT is complex and rapidly changing. Deciding which

Credhub keeps your credentials out of your configuration files. On a recent project, I was adding certificates and their private keys to a CredHub instance so that Concourse could retrieve them to configure and then deploy a Cloud Foundry foundation that would then use these certificates. To do this, I ran: credhub set –name /path/to/certificate

Photo by Aleksandar Radovanovic on Unsplash While using the PostgreSQL Helm Chart I wanted to take a look at the queries which were running. I quickly realized I needed to enable the logging to see all the DML goodness to later feed into pgBadger to review the usage patterns of the queries. Below are three

I’m deep in the weeds again. I’m inside of a YAML document inlined inside of a heredoc inside of a bash script that exists as a string inside of a heredoc inside of a Terraform configuration file written in HCL. It’s not my finest work, but it’s up there. To complete this masterpiece, I simply

This morning, I was trying to wrangle our CI/CD pipeline for the Containers BOSH Release so that I could cut a 1.1.0 release and generally forget about the process of integration testing. Our stock pipeline architecture for BOSH releases runs a deployment test by taking a manifest — either the example manifest or a CI-specific

help·ful/ˈhelpfəl/ Giving or ready to give help Useful Our executive team locked ourselves in a San Francisco apartment for two days this year and went through an exercise in defining who, what, and where we want to be as a company. The end result was a set of core values, an azimuth pointing towards the

At some point, we’ve all been in an environment similar to the one shown above and had the fun experience of SSHing from one Jumpbox to the next in order to access a deployment in a more secure environment. Now if this is a rare occurrence, it isn’t a big issue. The real annoyance comes
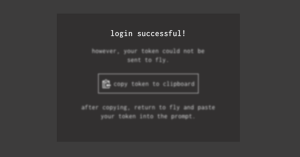
Authentication Scenarios When using Concourse in several environments, you’ll eventually end up in a situation where you’re on a remote system (Jumpbox, Docker Container, etc) and need to use fly to get or set a pipeline, or hijack into a job and troubleshoot a task. This is where things get a bit interesting. If you